Zero Trust Architecture: The Robust Security For A New World

Zero trust security architecture is emerging as an essential security model for reducing risk in a world of increasingly digital and remote workers. As the threat landscape rapidly evolves, companies are revisiting their security models to understand where their current architectures leave them vulnerable. The zero trust model is well suited for mobility and remote workforces, which is a growing trend in corporate environments.
The traditional network perimeter no longer exists in modern organizations – today, people travel across borders more than ever before. Identity is a core principle of zero trust security architectures. Once an asset is verified, it becomes part of an organization’s extended internal network (EDI). A zero trust security strategy uses the 80/20 rule to mitigate the risk of 20% of attacks that do 80% (or more) damage.”
Zero Trust Model
The zero trust model has been around for years, but it’s new to the cloud era. It’s an extension of the zero trust concept and helps organizations protect data in the world. Data that is increasingly digital, mobile, and remote from headquarters.
The threat landscape has changed significantly since traditional enterprise IT was built around physical servers located on-premises or within corporate networks. Today’s threats target all devices—not just computers running Windows or Linux versions of operating systems. And often bypass traditional firewalls by using encryption technology instead of passwords to access networks or data centers via virtual private networks (VPNs).
Also check: Best VPN Services To Use In 2022
These factors make it harder than ever before to enforce strict security policies across everything from laptops to smartphones. Employees can easily access sensitive information stored anywhere in their company without needing any credentials whatsoever when they connect through these devices during work hours. Even though they may not have had them at all times previously, due to only being able to access certain applications over shared connections.
Rather than direct connection streams between machines installed locally only accessible by specific users. Users who own them directly rather than being able to share those same resources with anyone else through Internet connections shared openly across an entire organization.”
Traditional Security Models are not Sufficient
Companies are realizing that traditional security models are not sufficient. They want a system that can scale and adapt as the threats grow more complex and sophisticated. They need a new approach that allows them to decentralize all aspects of their operations. While also providing end-to-end visibility across all devices, locations, and applications.
The zero trust model is well suited for mobility and remote workforces. It can also be used to support cloud computing, digital transformation, and other emerging technologies that are helping companies transform their business models while remaining agile and responsive to customer needs.
Zero Trust Architecture: How Does It Work?
The zero trust architecture works by defining different levels of trust between users who access applications or data within your organization. For example, You might have an account that allows you read-only access to some information stored in another server (e.g., Salesforce). In this case, you would create an additional account called “Read Only User” which has no permissions on any sensitive data. But only lets them see what they need without being able to modify anything or make changes themselves
The traditional network perimeter no longer exists in modern organizations
In the new world, we no longer live in a perimeter-based security model.
The traditional network perimeter has been replaced with a series of concentric circles. Which connect your organization’s endpoints and applications at layer 2 (the data link layer) or layer 3 (the network layer). These concentric circles can be thought of as “borders” around your organization. They represent physical boundaries between networks that must be protected against intrusion by external attackers. The most common types include DMZs and firewalls, but there are many more variations on this theme as well!
While each type has its own benefits and drawbacks, all rely on an outer protective barrier for their effectiveness rather than relying solely on internal controls such as policies/configurations/proxies, etc.
Identity is a core principle of zero trust security architectures.
Identity is the first line of defense for any security architecture. It’s the foundation of trust, and it’s a core principle of zero trust security architectures.
Once an asset is verified, it becomes part of an organization’s extended internal network. This verification process ensures that the asset is secure and will remain so throughout its lifecycle. The process involves three steps:
- First, the asset needs to be analyzed by security professionals who will identify possible threats against it.
- Next, these experts must determine how best to mitigate those threats. Before they can be exploited by malicious actors or even humans who accidentally click on a phishing email or open up a malicious attachment in their Gmail inboxes.
- Finally—and importantly—the security team must implement controls over access. So only authorized users have access rights when handling sensitive data. Data such as passwords or financial information is stored on servers within each organization’s Network Operations Center (NOC).
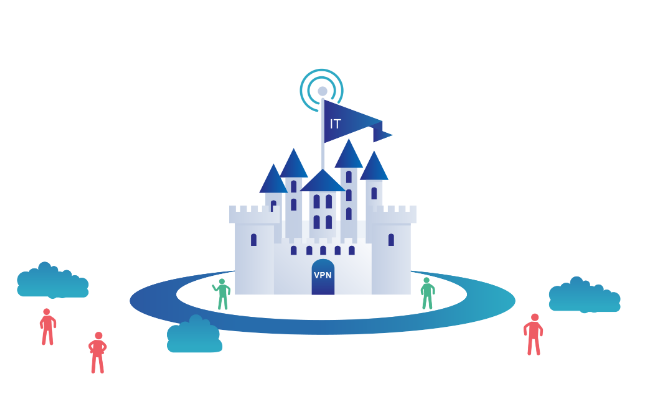
A zero trust security strategy uses the 80/20 rule
A zero trust security strategy uses the 80/20 rule to mitigate the risk of 20% of attacks that do 80% of damage.
The 80/20 rule states that 20% of your customers account for 80% of your revenue. The same principle applies to IT infrastructure. You need to only worry about maintaining a small percentage of things. In order to prevent having to deal with all kinds of problems related to them, such as data loss or exposure.
Zero trust architecture is an approach that uses this principle by defining what constitutes “trusted” and “untrusted” data based on an audit trail (that includes metadata). So users can make decisions about whether or not they want to access it. Without having any information about where their data comes from or what could happen if it were compromised.
Zero trust security architecture can help you adopt remote work strategies. While protecting critical data from being compromised by unauthorized access or even destruction.
How to implement Zero Trust Security?
The implementation of a zero-trust network is not as complex as it may sound. And also, it is a cost-effective technique to avoid any major losses from a security breach. Or any unauthorized access to the network.
1. Network segmentation
The first thing you need to do is to create different networks for different purposes. For example, if you have a large network and want to keep it secure from hackers. Then it is better to divide your network into smaller networks and assign each network with a specific purpose.
For example, if you want to build an internal network for your employees and an external network for your partners and customers. Then you can simply create two separate networks using different protocols such as DMZ or VLANs.
2. A robust access management system
If you are using multiple protocols on the same firewall device, then you need an access control mechanism. That will allow only authorized users to access the system. You can also use some form of authentication mechanism like Kerberos or PAM which is used by many organizations these days.
3. Minimizing privileges at the firewall
In order to prevent unauthorized users from accessing any part of your network, always keep in mind that there should be the least possible number of privileges granted to every user on your firewall device. So that no one can get more than what they need while other users cannot get anything either because they are not allowed by their role.
4. Application Context to Firewall
Application context to the firewall is another essential element in implementing Zero Trust Security. Because it enables you to monitor traffic from any application on your network. Even if it is not logged into any database or database server. The analytical capabilities of firewalls are also crucial for analyzing security events. That may occur in real-time or after some time interval.
5. Analyzing Security events
Cyber security analysts can work efficiently only when they have acquired data that can be used for drawing insights and conclusions. Hence, many organizations use security information and event management solution that helps them to draw conclusion and correlations out of huge chunks of data.
Conclusion
Zero trust architecture is a framework that allows companies to adopt new technology while protecting critical data. Zero trust security architectures enable companies to adopt remote work strategies. Which can help them avoid the costly consequences of compromised assets or sensitive information being leaked. These architectures also allow for hybrid IT environments where employees are connected both physically and digitally.